SSO setup and JIT provisioning: BMS and Passly
Introduction
This article covers the Auth setup with BMS and Passly. Follow this guide to setup, SSO, SAML, and Just in time provisioning using Passly and BMS.
Single sign-on with Passly
This section covers how to configure BMS to authenticate users with Passly using SAML-based Single Sign-On (SSO).
Create Passly group
You need to have a Passly user group to associate with the BMS SSO configuration.
- In Passly, navigate to Directory Manager > Groups.
- Click the '+' button to create a new group.
- Give a name to your group.
- Click the Add Group button.
- Add users to the group.
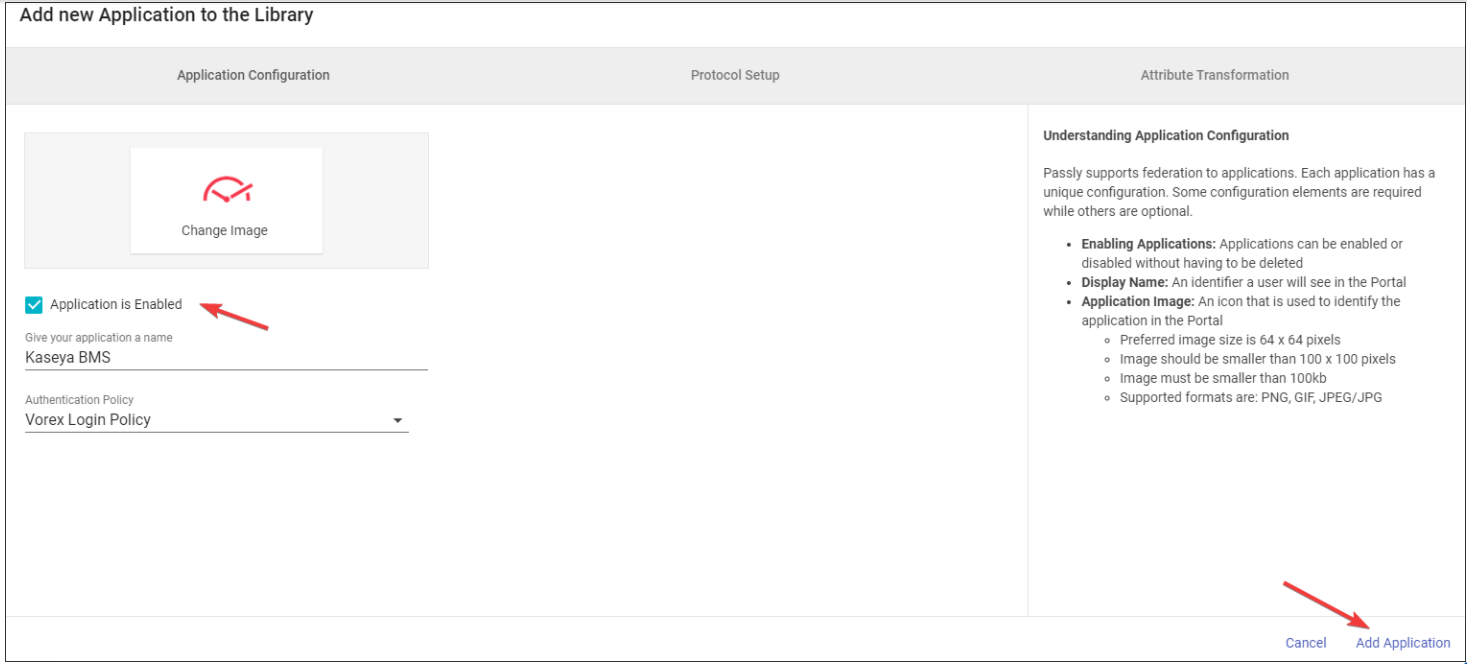
Add BMS to Passly
- Navigate to SSO Manager.
- Click the '+' button followed by the book button.
- Search for 'Kaseya BMS' in the application catalog and select it.
- Check Application is Enabled.
- Click Add Application.
Permissions
- Navigate to the Permissions tab.
- Click Add Group.
- Select the group you created previously.
- Click Add Groups.
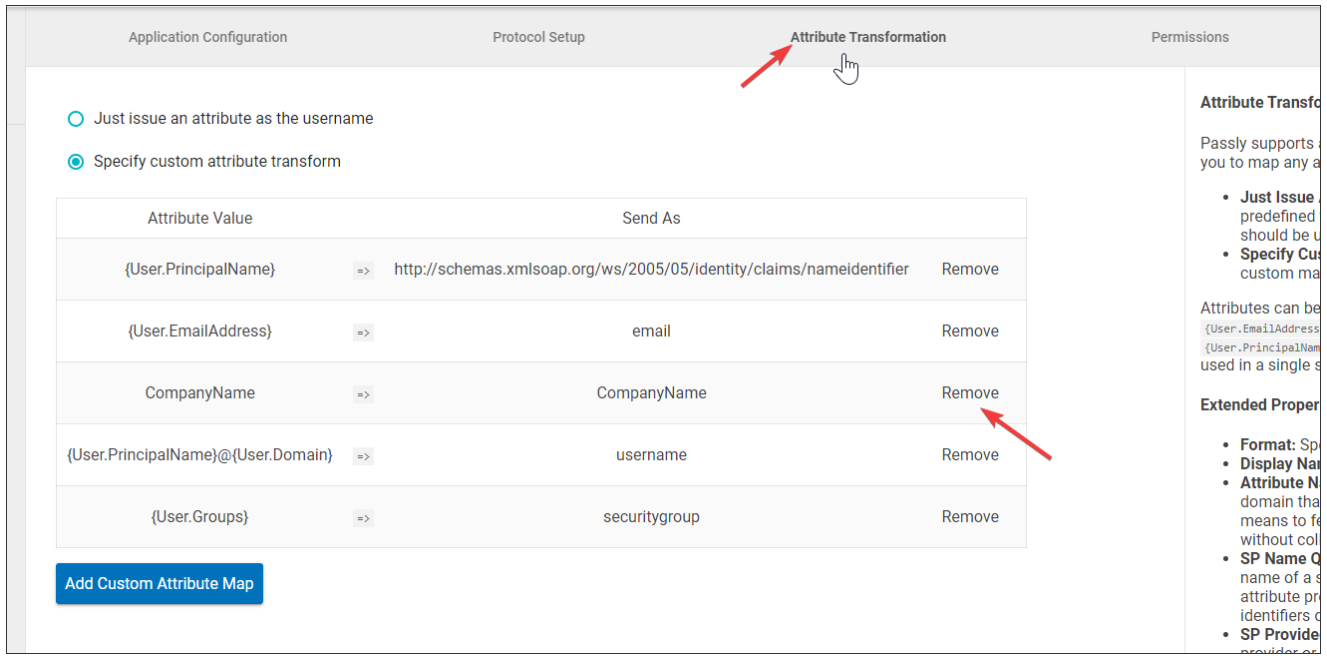
Attribute Transformation
- Navigate to the Attribute Transformation tab.
- Remove the CompanyName attribute.
- Save your changes.
- Click Add Custom Attribute Map.
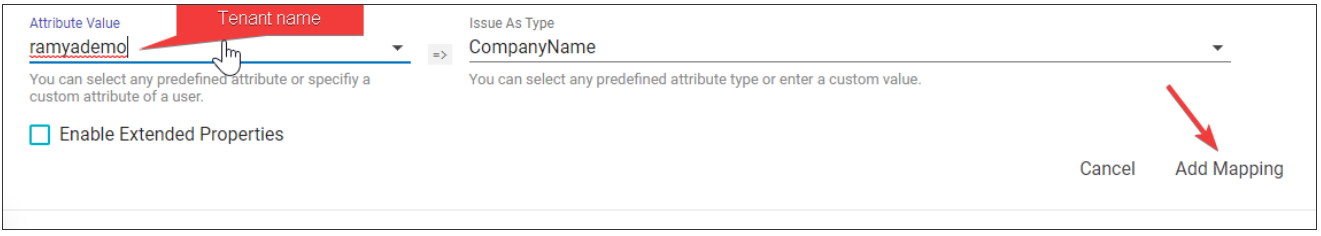
- Add back the CompanyName attribute, referencing your tenant name.
- Click Add Mapping.
- Save your changes.
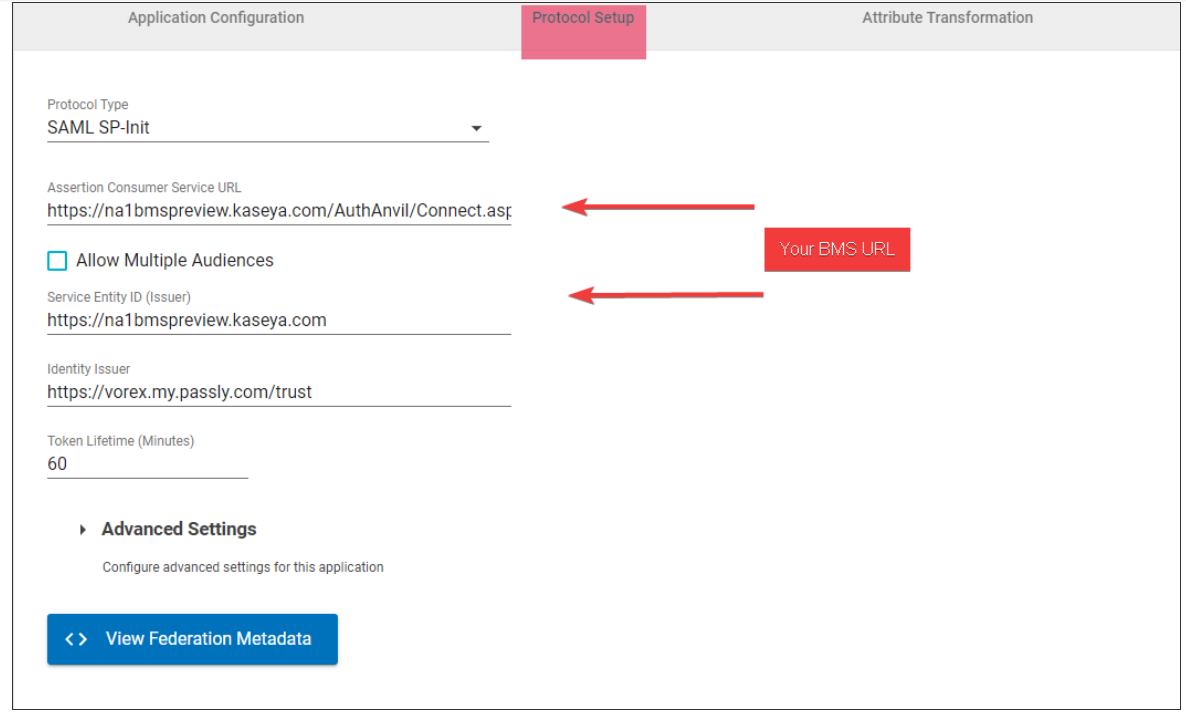
Protocol Setup
- Navigate to the Protocol Setup tab.
- For Assertion Consumer URL, change the base url to the base url of your BMS server. In the example below, the base url is na1bmspreview.kaseya.com.
- For Service Entity ID, change the base url to the base url of your BMS server. In the example below, the base url is na1bmspreview.kaseya.com.
- Save your changes.
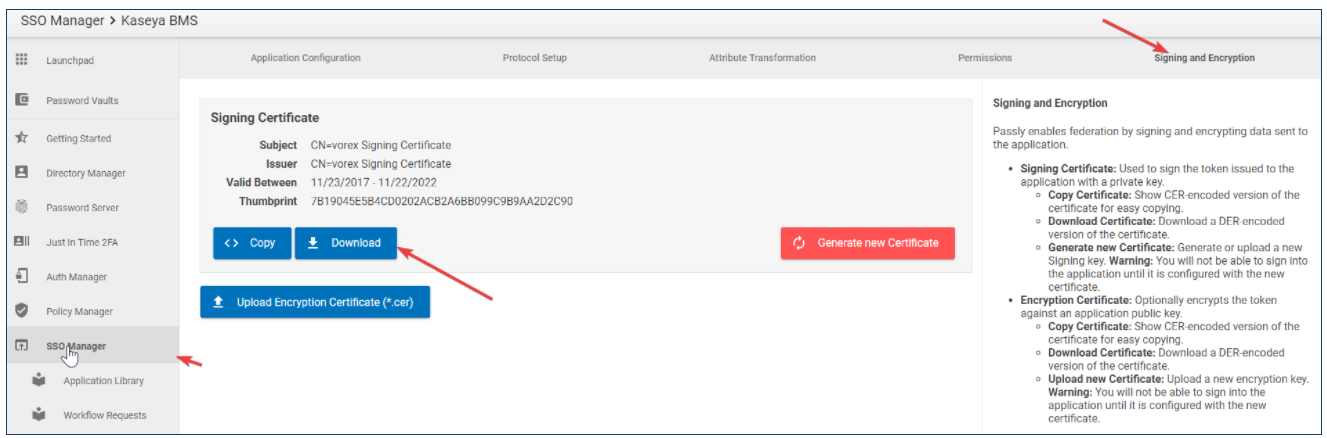
Download certificate
- Navigate to the Signing and Encryption tab.
- Click Download.
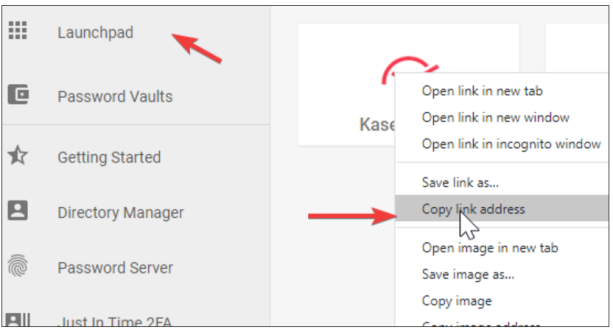
Passly application assignment
- Navigate to Launchpad in the left menu.
- Right-click on the BMS application, and copy the link to a text pad.
- Click on the BMS application.
- Verify that you are redirected and logged in to BMS.
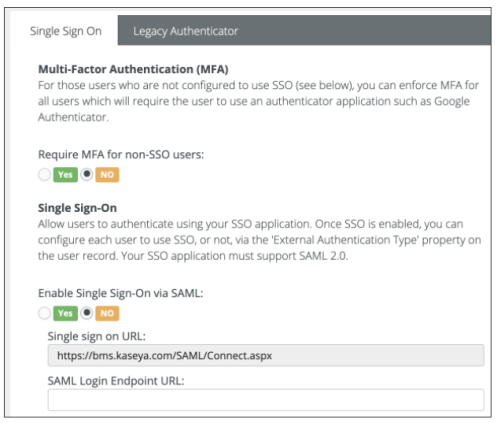
Setup BMS SSO
- In BMS, navigate to Admin > My Company > Auth and Provision.
- On the Single Sign On tab, click Upload Certificate.
- Select the Passly certificate you previously downloaded.
- Set Enable Single Sign On via SAML to Yes.
- Paste the Passly login url you copied above into the SAML Login Endpoint URL field. This enables user authentication with Passly from the BMS login page.
- Click Save.
Enable SSO for employees
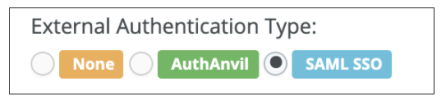
- Navigate to HR > Employees.
- Select an employee.
- Under External Authentication Type, select SAML SSO.
Just-in-time (JIT) provisioning is a method of application account creation. JIT is integration with your active directory services, your IDP (Passly), and your web application (BMS).
With the implementation of JIT with BMS, AD users are created and provisioned during their sign-on to the BMS portal. This eliminates the need for manual user creation and automates employee/end-user onboarding effectively.
To set up your JIT directory with BMS perform the following steps :
Prerequisites in Passly
- SAML based single sign-on enabled.
- The end-user/groups should have the SAML app assigned in Passly Applications.
- The Domain and security groups should be present and match the mapping rules setup in BMS
- User account should have an email address associated with it.
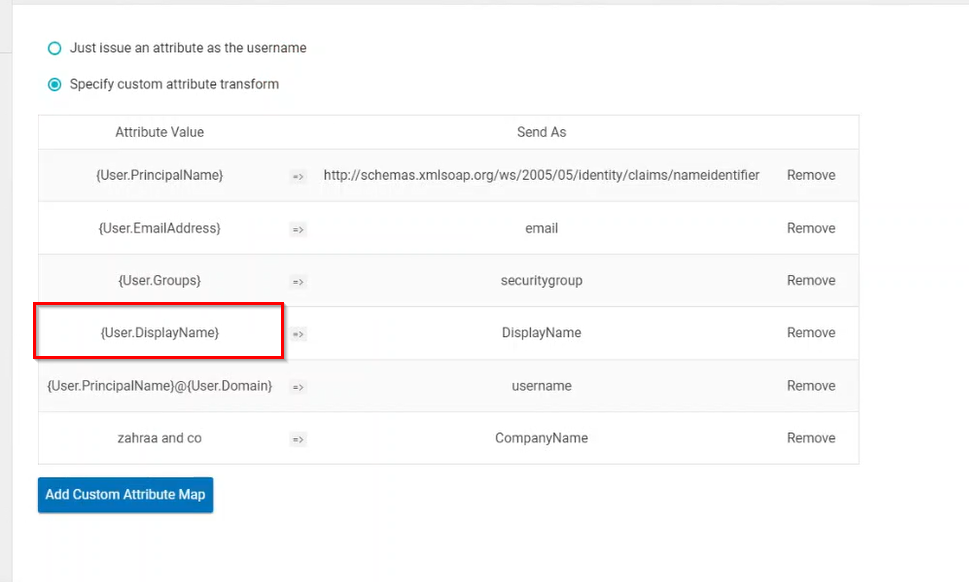
Enable JIT provisioning
An additional attribute, DisplayName needs to be added in Passly for JIT provisioning.
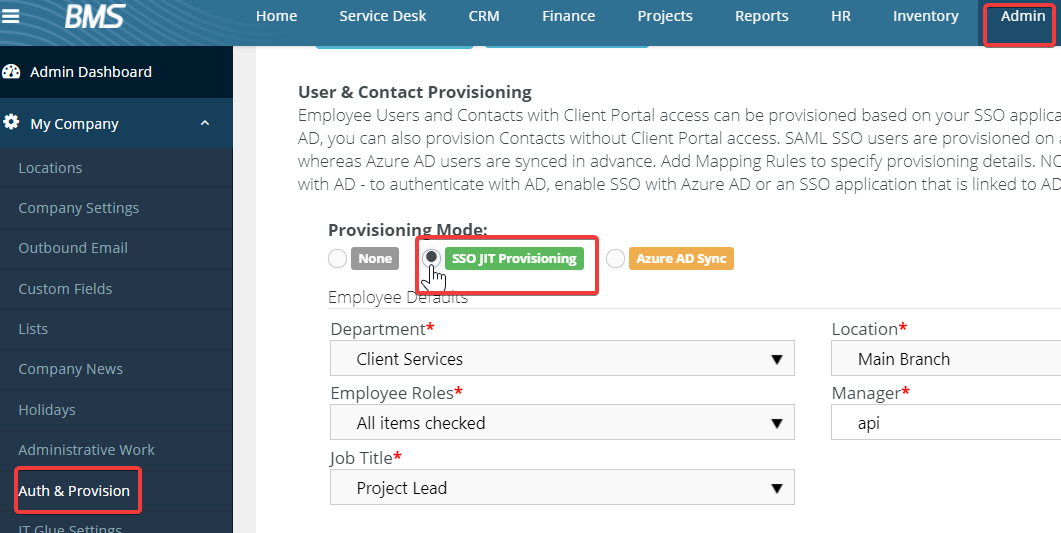
Just-in-Time (JIT) provisioning is set up on the BMS Authentication page
- In BMS, navigate to Admin > My Company > Auth and Provision.
- Choose SSO JIT Provisioning.
- Set default values under Employee Defaults, these will be assigned to the users being provisioned.
- Add Mapping Rules to start provisioning Active Directory Groups to BMS.
- Multiple rules can be added to establish mapping for different security groups.
- Save your settings.
- Users will be auto-provisioned based on your Active Directory Domain, Security group/User mappings to BMS.
- The provisioned user will be attached to the account defined in Employee defaults.
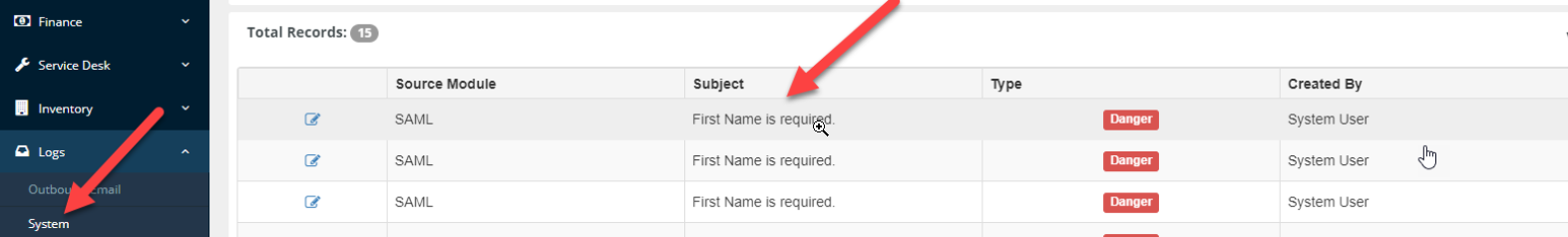
Logs
For any issues with heck the logs to see the error messages for any issues with JIT or SAML.
Navigate to Admin > Logs > System, review the logs for source SAML and you will see where the setup is failing.